From malware.news
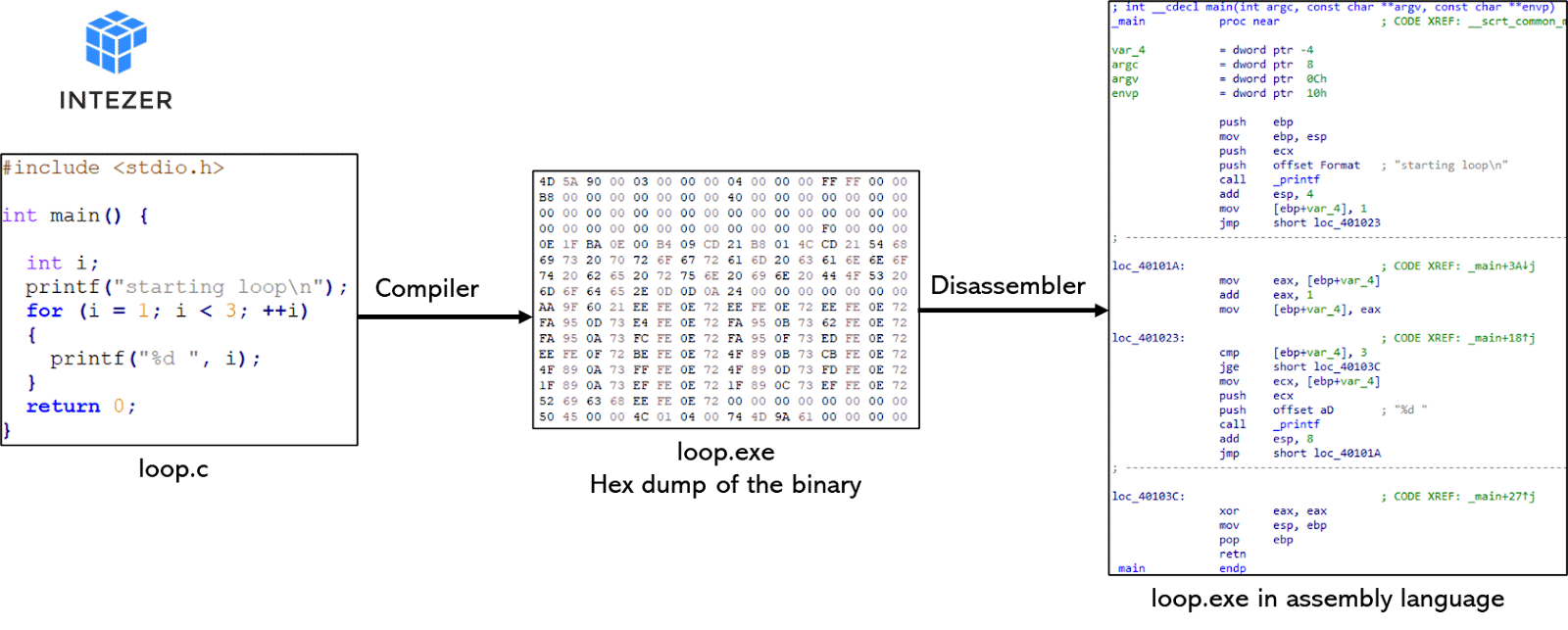
Malware researchers require a diverse skill set usually gained over time through experience and self-training. Reverse engineering (RE) is an integral part of malware analysis and research but it is also one of the most advanced skills a researcher can have. This is one of the reasons why organizations lack reverse engineering manpower. Many researchers with a lack of experience struggle to get started in RE. Gaining a solid starting point in RE with the relevant knowledge and terminologies can be a differentiator for a researcher.
This series will provide RE basics for malware researchers, analysts and IR experts who have no reverse engineering experience but wish to learn how. In Part 1, you will learn about basic computing terms and assembly language.