From thehackernews.com
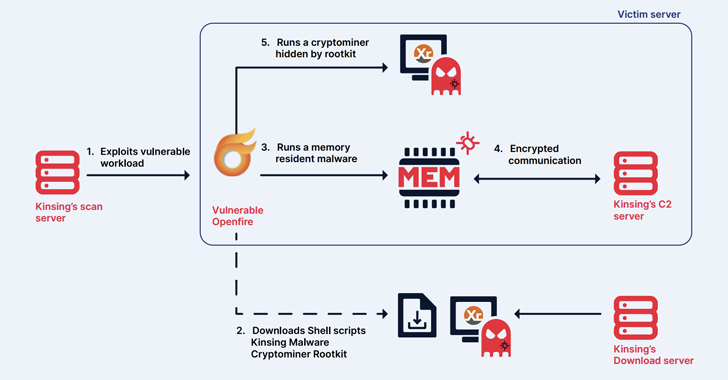
The cryptojacking group known as Kinsing has demonstrated an ability to continuously evolve and adapt, proving to be a persistent threat by swiftly integrating newly disclosed vulnerabilities to the exploit arsenal and expand its botnet.
The findings come from cloud security firm Aqua, which described the threat actor as actively orchestrating illicit cryptocurrency mining campaigns since 2019.
Kinsing (aka H2Miner), a name given to both the malware and the adversary behind it, has consistently expanded its toolkit with new exploits to enroll infected systems in a crypto-mining botnet. It was first documented by TrustedSec in January 2020.
In recent years, campaigns involving the Golang-based malware have weaponized various flaws in Apache ActiveMQ, Apache Log4j, Apache NiFi, Atlassian Confluence, Citrix, Liferay Portal, Linux, Openfire, Oracle WebLogic Server, and SaltStack to breach vulnerable systems.
Other methods have also involved exploiting misconfigured Docker, PostgreSQL, and Redis instances to obtain initial access, after which the endpoints are marshaled into a botnet for crypto-mining, but not before disabling security services and removing rival miners already installed on the hosts.
Subsequent analysis by CyberArk in 2021 unearthed commonalities between Kinsing and another malware called NSPPS, concluding that both the strains “represent the same family.”