From securityonline.info
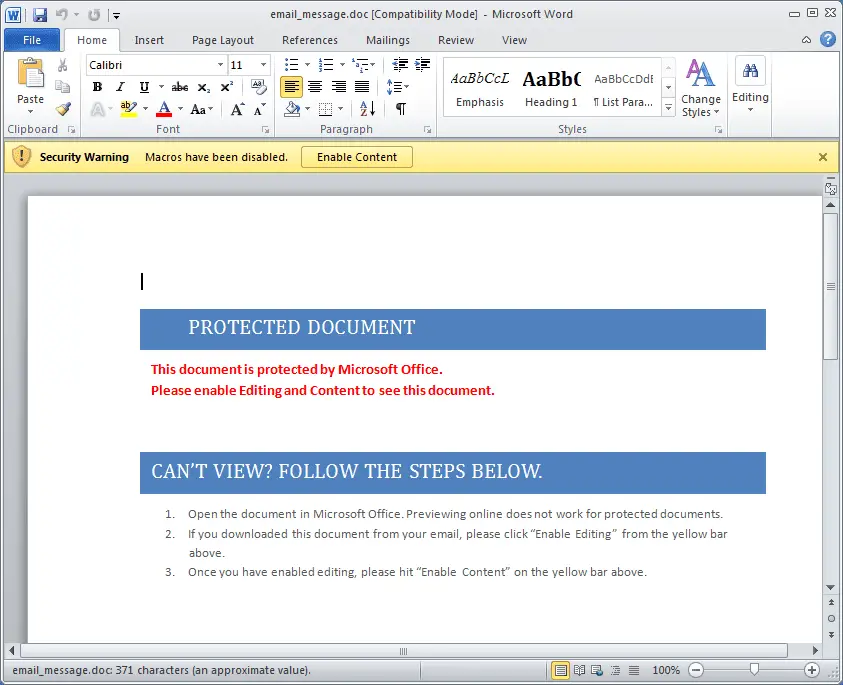
Features
- Insert tracking pixels into Office Open XML documents (Word and Excel)
- Inject template URL for a remote template injection attack
- Inspect external target URLs and metadata
- Create Office Open XML documents (#TODO)
From securityonline.info
