From hackersonlineclub.com

Tails is a portable LIVE operating system that protects your privacy and helps you avoid censorship.
LEAVE NO TRACE. Tails uses the Tor network to protect your privacy online. It is based on Debian GNU/Linux.
From hackersonlineclub.com

Tails is a portable LIVE operating system that protects your privacy and helps you avoid censorship.
LEAVE NO TRACE. Tails uses the Tor network to protect your privacy online. It is based on Debian GNU/Linux.
From securityaffairs.co

Netgear is addressing ten vulnerabilities affecting nearly 80 of its products, including issues discovered at the Pwn2Own hacking competition.
Netgear is releasing security patches to address ten vulnerabilities affecting nearly 80 of its products. Some of the vulnerabilities were discovered during the Pwn2Own Tokyo 2019 hacking contest and reported through the Zero Day Initiative (ZDI). The researchers earned a total of $25,000 for reporting them.
Netgear published the list of impacted products, it includes routers, mobile routers, modems, gateways and extenders. Some of the products have reached end of life (EOL), this means that the vendor will not release security updates the fix for these flaws.
From securityboulevard.com

For as long as they’ve existed, web applications have been a favorite target for hackers. They are relatively easy to break and give hackers potential access to sensitive information as well as serving as an entry point to an otherwise well-protected system.
Last year, an investigation into data breaches by Verizon found that web applications are among the top three attack vectors across eight of the nine industry verticals studied. Moreover, web applications took the leading spot in four of those vertical sectors.
From bleepingcomputer.com

The U.S. Federal Reserve today issued guidance on how financial organizations from the United States can mitigate payment fraud attempts scammers carry out with the help of synthetic identity accounts.
The white paper published today by the Federal Reserve on mitigating synthetic identity payments fraud comes after two previous white papers on defining and detecting such payments fraud attempts.
Synthetic identities are created by fraudsters after combining real information (like Social Security Numbers) and fake information (names, dates of birth, and addresses).
From zdnet.com

In one of the biggest password re-use studies of its kind, an analysis of more than one billion leaked credentials has discovered that one out of every 142 passwords is the classic “123456” string.
The study, carried out last month by computer engineering student Ata Hakçıl, analyzed username and password combinations that leaked online after data breaches at various companies.
From ehackingnews.com

For the past year and a half, a rather small group of activists known as Distributed Denial of Secrets, or DDoSecrets, has discreetly yet consistently released a flood of hacked and leaked documents, from Russian oligarchs’ emails to the stolen communications of Chilean military leaders to shell company databases.
From malware.news
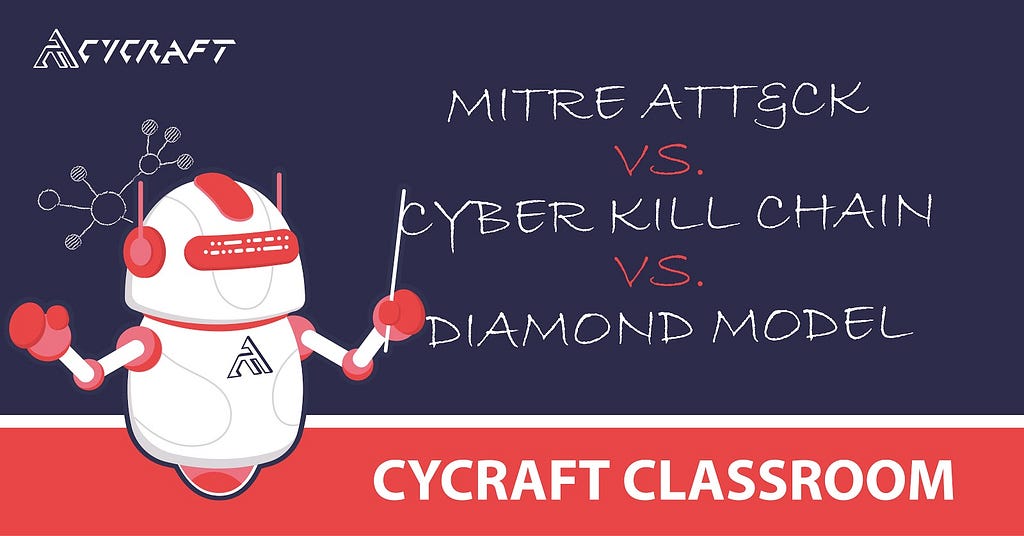
In cybersecurity, there have been several approaches used to track and analyze the various characteristics of cyber intrusions by advanced threat actors.
1. Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill ChainsIn 2011, the US Department of Defense officially incorporated cyberspace as a component of the fifth domain of warfare, Information Operations; the first four consisting of land, sea, air, and space.The defense contractor, Lockheed Martin, extended the military concept of a kill chain and adapted it to cybersecurity. The Cyber Kill Chain, as it is currently called, breaks down an intrusion into a well-defined sequence of seven phases from Reconnaissance to Actions on Objectives.