From hackread.com
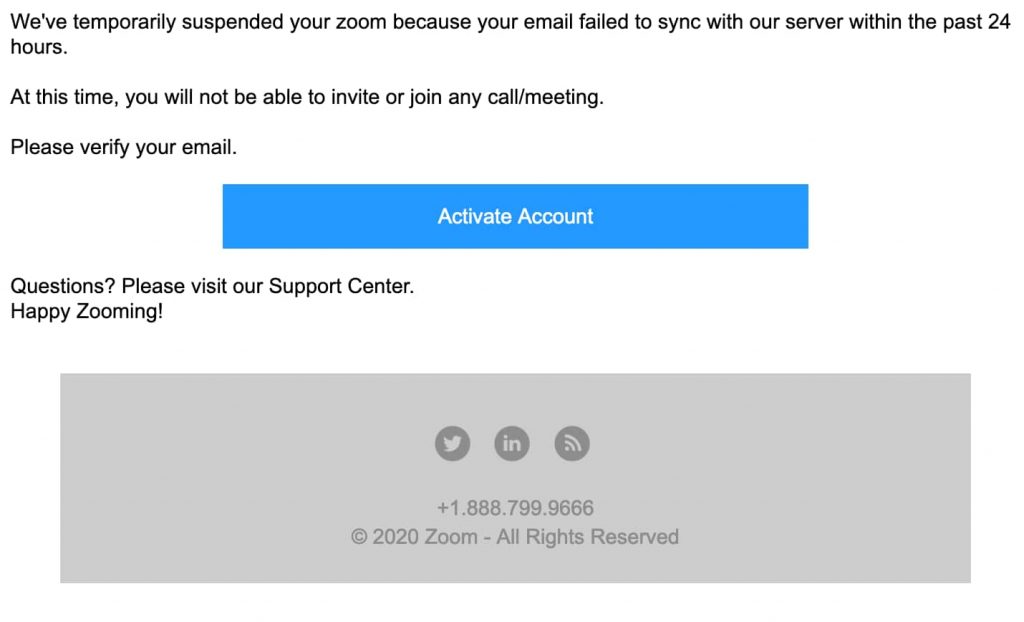
The phishing scam targets victims by claiming that their Zoom account has been suspended.
Microsoft enamors 44 million daily active users due to the global pandemic. Not only this but in the last month, daily users have jumped a whopping 70 percent and have gone up to 75 million active users. Whereas, Zoom on its run to ensue transparency, claims ‘300 million daily Zoom meeting participants worldwide’.
The pandemic has shifted organizational dynamics to digital platforms. Social distancing has led to an uber need to integrate tools with office teams using cloud applications.



