From infosecurity-magazine.com

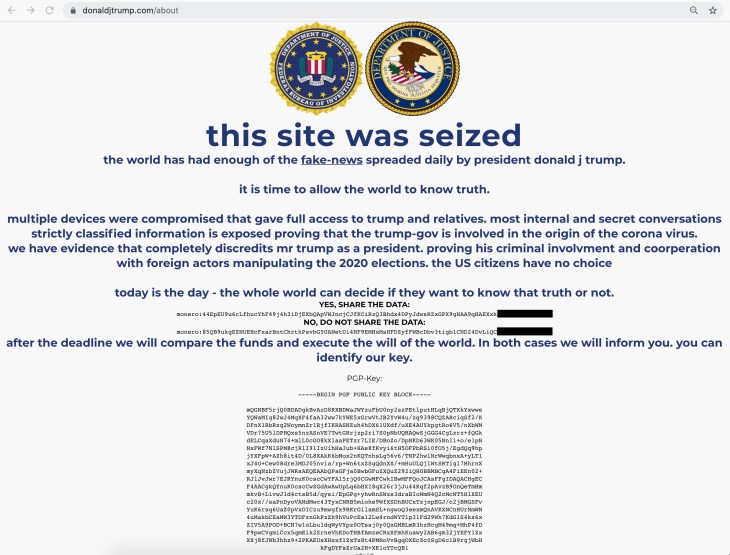
Amazon has sent emails to users warning of a rogue insider who has been fired after disclosing customer details to a third party.
As detailed in a tweet posted by user Zain Jaffer, the email read: “We are writing to let you know your email address was disclosed by an Amazon employee to a third party in violation of our policies.” The email goes on to claim the employee has been fired, referred to law enforcement and stated that no other information related to the recipient’s account was shared.
“This is not a result of anything you have done and there is no need for you to take any action, we apologize for this incident,” it continued.