From 2-spyware.com
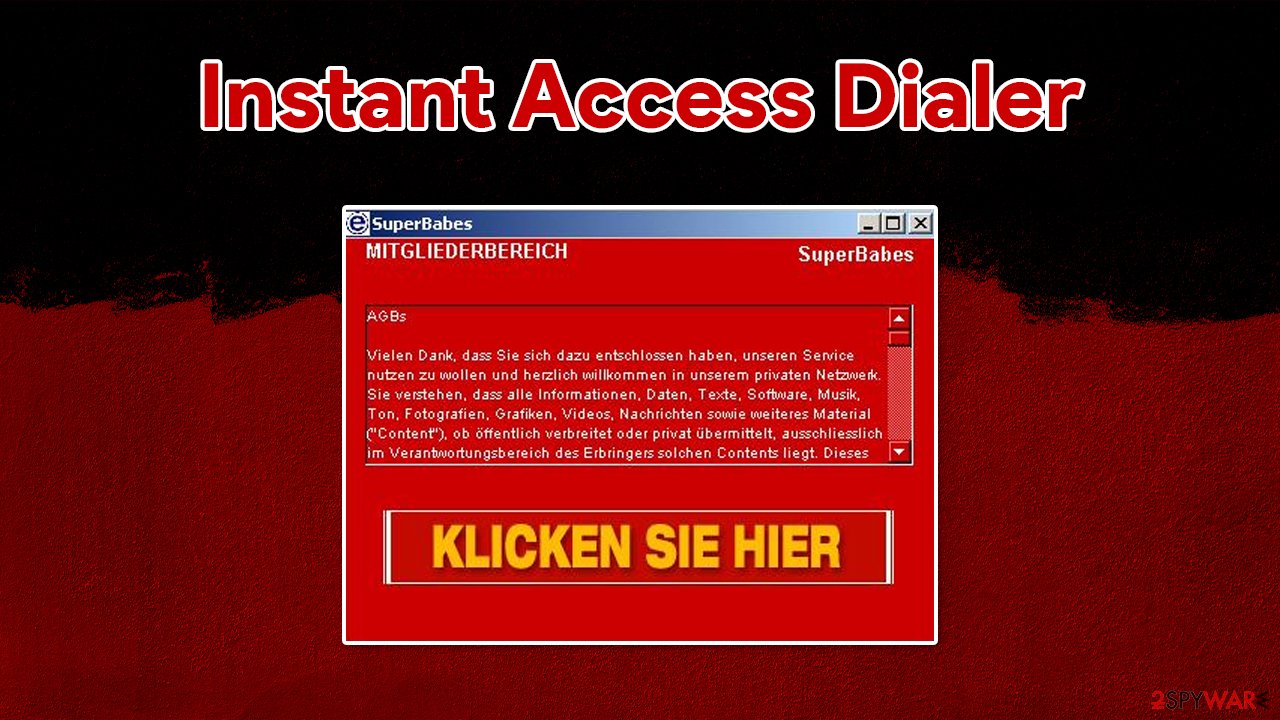
Instant Access Dialer, otherwise known as Dialer:Win32/InstantAccess, is a malicious program that is designed to change the settings of a dialup connection. By doing so, the virus is able to automatically connect to a website that uses premium dialup costs, consequently resulting in serious financial losses for the victim.
If you are using a dialup connection for your internet, this malware is a dangerous threat for you, and you should take precautionary measures to avoid it in the future. If you are already infected, check the information in this article in order to restore your normal settings and remove the Instant Access Dialer virus for good.




