From blogs.cisco.com
NIST CSF Categories and Sub-Categories
IDENTIFY – Asset Management (H/W and S/W inventories; communication and data flow mapping)
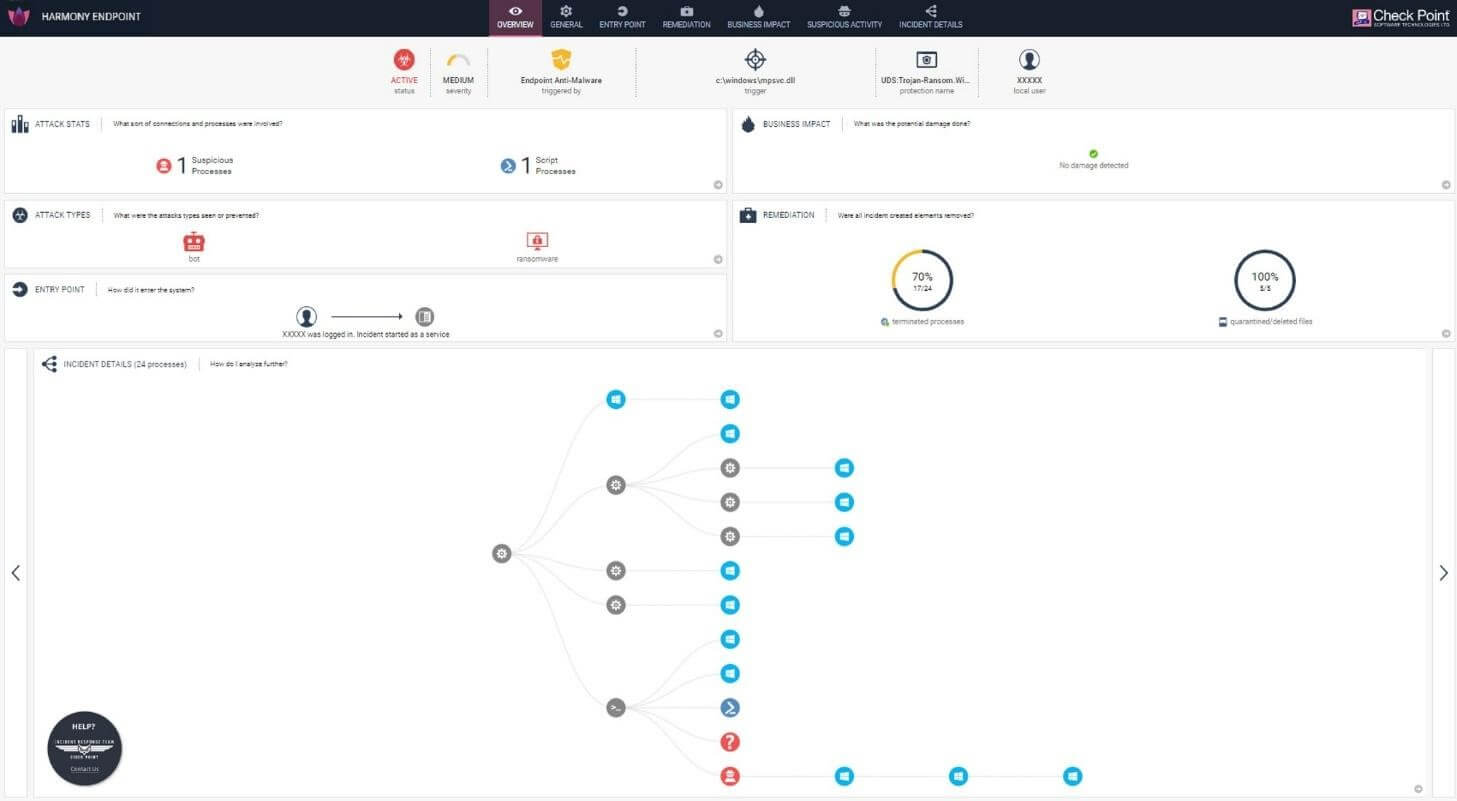
[ID.AM-1 and ID.AM-2] Orbital gives detailed information about the H/W and running applications/processes by querying endpoints using WMI. It can also help in tracking disk space, memory and any other IT Ops artifacts. All this information can then be used to create H/W and S/W inventories for the organisation. Secure Endpoint can also be used to check system status (OS versions, patches, if host firewall is enabled, what application is allowed through etc).
IDENTIFY – Risk Assessment (vulnerabilities identified; threat intelligence received; threats identified; threats, vulnerabilities and impacts to determine risk)