From securityaffairs.co

Microsoft rolled out KB5004945 emergency update to address the actively exploited PrintNightmare zero-day vulnerability (CVE-2021-34527) in Print Spooler service.
From securityaffairs.co

Microsoft rolled out KB5004945 emergency update to address the actively exploited PrintNightmare zero-day vulnerability (CVE-2021-34527) in Print Spooler service.
From theregister.com
Kaseya’s attempt to recover its SaaS services has failed, and its CEO has attempted to play down the significance of the incident that has seen its VSA services offline since July 2nd and over 1,000 ransomware infections.
The biz, which makes system monitoring and management software for IT service providers, issued an update at 10PM Eastern Daylight time (EDT) on July 6th that stated:During the VSA SaaS deployment, an issue was discovered that has blocked the release. Unfortunately, the VSA SaaS rollout will not be completed in the previously communicated timeline.
From helpnetsecurity.com
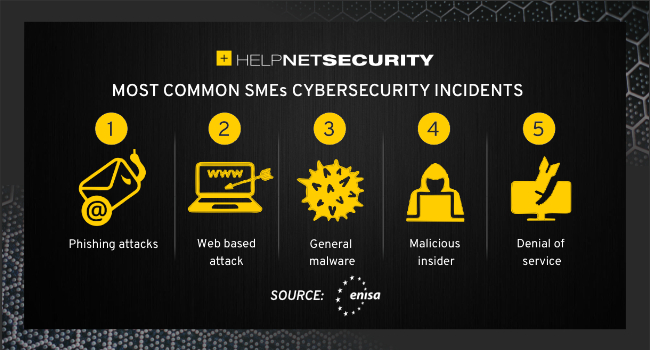
Small and medium-sized enterprises (SMEs) are considered to be the backbone of Europe’s economy. 25 million SMEs are active in the EU, and employ more than 100 million workers. ENISA identified the cybersecurity challenges SMEs face today and issued recommendations.
From gbhackers.com

Recently, in a joint warning, the cybersecurity agencies of the US and UK have released a set of large-scale brute-force attacks escorted by the Russia-linked APT28 hacking group.
There were many other groups that have been tracked in this attack like, Fancy Bear, Pawn Storm, Sednit, Strontium, and Tsar Team. Not only this, even all these groups have attacked many organizations all over the world.
The report of NSA pronounced that the brute force attacks that have been detected have the ability that enables the 85th GTsSS threat actors to access guarded data, that involves email, and identify valid account credentials.
From techrepublic.com
The same powerful tool used by organizations to enhance their security is being adopted by cybercriminals to help break through their security. Popular penetration testing program Cobalt Strike saw a 161% increase in malicious use from 2019 to 2020 and is considered a high-volume threat for 2021, according to a report released Tuesday by security provider Proofpoint.
From malware.news

The ASEC analysis team is using the ASEC automatic analysis system RAPIT to categorize and respond to known malware. This post will list weekly statistics collected from June 21st, 2021 (Monday) to June 27th, 2021 (Sunday).
For the main category, info-stealer ranked top with 68.2%, followed by RAT (Remote Administration Tool) malware with 21.7%, DDoS with 3.9%, downloader with 3.1%, and ransomware with 2.2%.
From helpnetsecurity.com

Active Directory (AD), a directory service developed by Microsoft for Windows domain networks, is most organizations’ primary store for employee authentication and identity management, and controls which assets / applications / systems a user has access to. This makes Active Directory a valuable target for attackers and spur organizations to improve its security.
But Guido Grillenmeier says that the technology has been dropped from the corporate agenda.