From cybersecuritynews.com
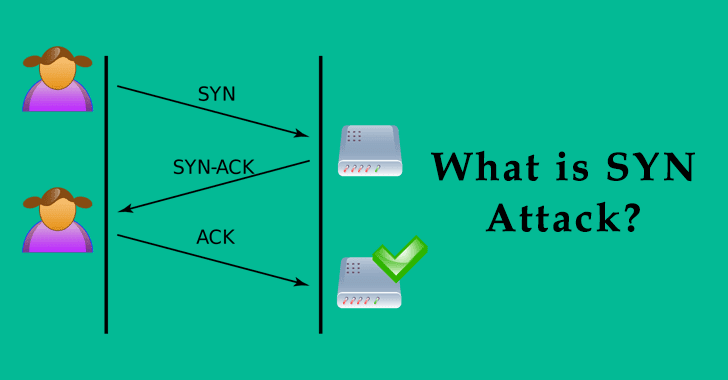
TCP SYN Flood attacks are the most popular ones amongst the DDOS attacks. Here we are going to discuss in detail, the basis of the TCP SYN attack and to stop before it reaches those servers.
It’s been more than two decades when the first DDOS attack was attempted at the University of Minnesota which knocked it down for two days. A lot followed that, including one of the biggest in history of DDOS which was against Github and involved 1.35 TBps attack against the site.