From securityboulevard.com

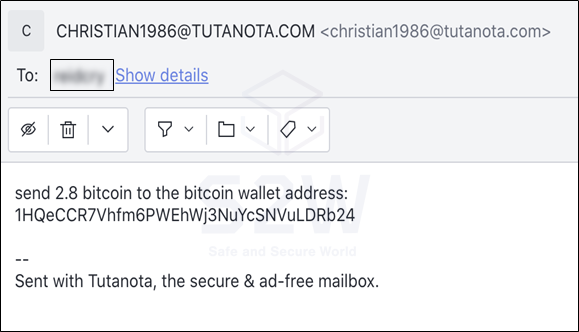
As the global financial services industry undergoes a seismic shift, disruption is prompting the industry to replace traditional practices, with emphasis on the inevitable digital future banks will have to embrace.
In a report from Deloitte, nearly three-quarters (73%) of respondents said they fear their organizations would lose competitive advantage if they fail to adopt blockchain and digital assets.
However, even as new payment options represent a “very important” role for digital assets in their organizations, there are a multitude of cybersecurity issues looming unresolved on the horizon.