From 2-spyware.com
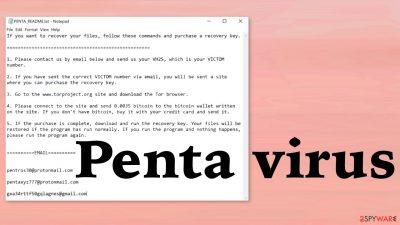
Penta ransomware is a virus that encodes original data and changes the name to indicate that the piece is affected. The process happens quickly, so the infection is not noticed before it is too late. Once the virus is done locking data, it provides the PENTA_READ_ME.txt ransom note with further instructions and tips for the victim. The purpose of such a message is to encourage people to pay up since the main goal of criminals behind these threats is money. Creators claim that cryptocurrency transaction is the only method to get those files back, but it is not recommended to even contact criminals behind the infection. You may receive additional malware instead of the proper decryption tools or any helpful application or solution.




