From: independent.co.uk
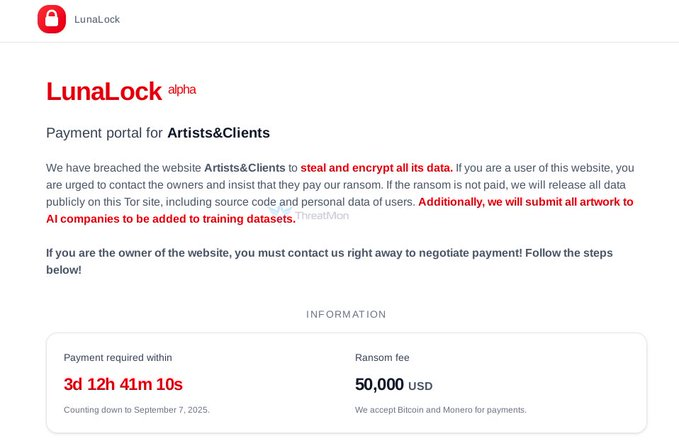
Flights have been delayed and cancelled at several European airports after a cyber attack targeting a service provider for check-in and boarding systems.
The attack has rendered automated systems inoperable, allowing only manual check-in and boarding procedures, according to Brussels Airport.
London Heathrow and Berlin airport also said the attack was disrupting its flights, with passengers advised to confirm their travel with airlines before heading to the airport on Saturday.