From indusface.com
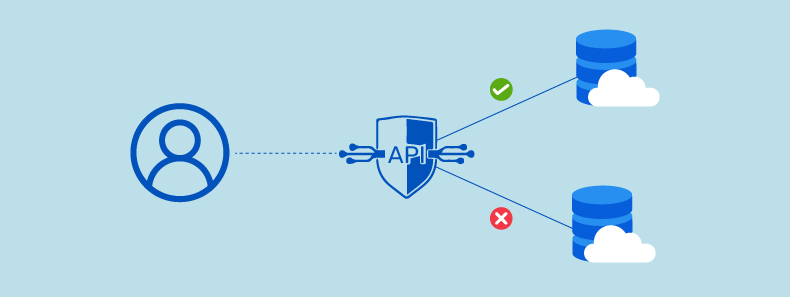
Hacks and data leaks have affected many major players in recent years, including AT&T Vendor(9 Million accounts), T-Mobile (37 Million accounts), JD Sports(10 Million), MyDeal (2.2Million), Dropbox (nearly 69 million accounts), Flagstar bank (1.5 Million) and eBay (145 million).
Those were bad. But not the worst. What are the most notorious hacks in history? They’re subject to debate, but these 23 attacks categorized under OWASP Top 10 would be strong candidates for the title.



