From neurosoft.gr
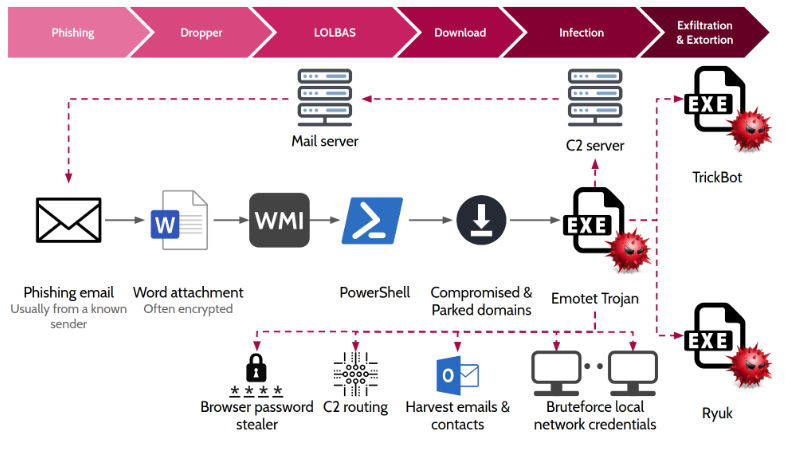
Emotet is considered to be among the top malware threats, primarily spreading through emails and specifically using the email thread hijacking approach. In this latest report, researchers from University of Piraeus, Athena Research Center and Neurosoft have dissected the malware and conducted an in depth analysis of the Emotet campaign.
