(Image from Google Gemini.)
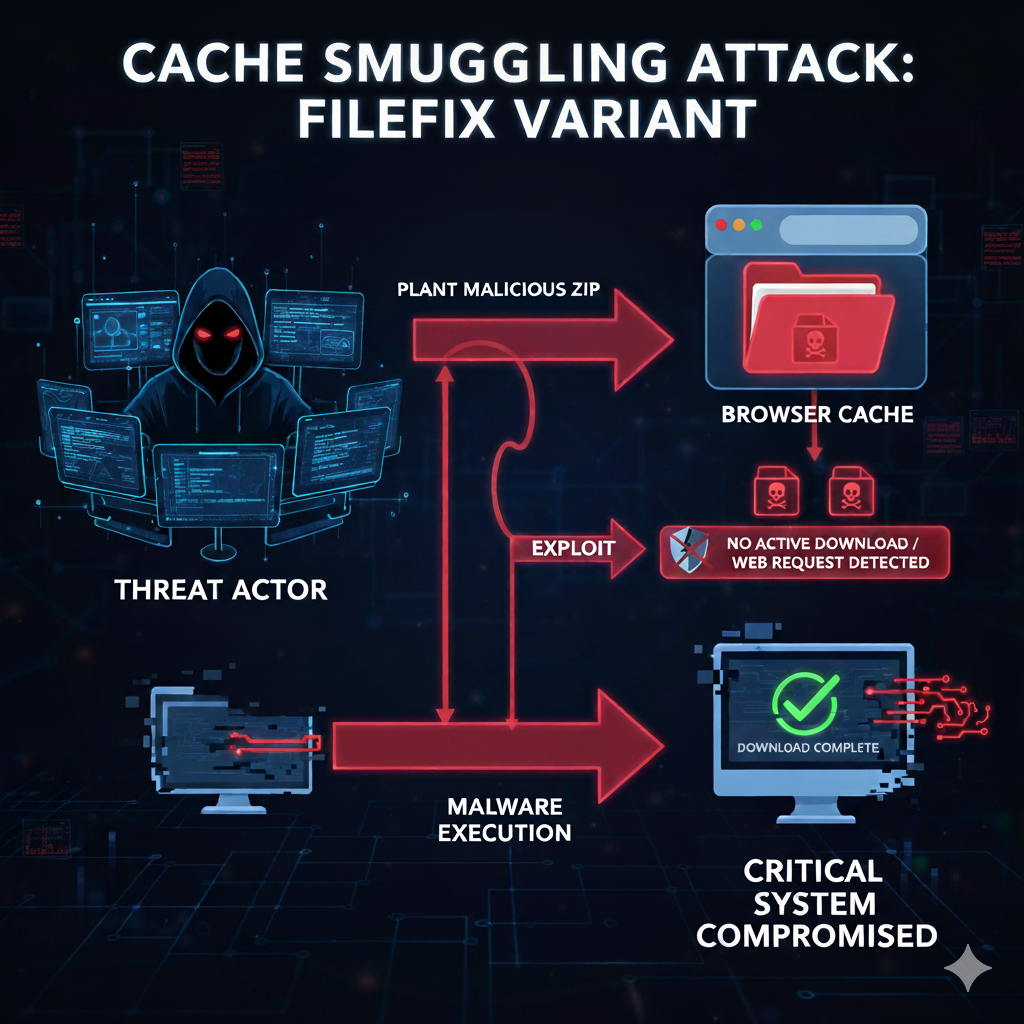
BLUF: Threat actors are using a sophisticated variant of the FileFix social engineering attack, known as cache smuggling. It plants malicious ZIP archives in a victim’s browser cache. This enables execution of malware while bypassing security software checks for active file downloads or web requests.
The new FileFix campaign lures victims with a spoofed tool such as “Fortinet VPN Compliance Checker.” The user is told to copy a seemingly innocuous network file path and paste it into the Windows File Explorer address bar.
However, the text copied to the clipboard is heavily padded with spaces, concealing a malicious PowerShell command that is executed in headless mode when the user presses Enter.
The principle behind the attack is ‘cache smuggling’. When the user accesses the phishing page for the first time, JavaScript requests the browser to fetch a payload which has been disguised as a legitimate JPEG image. The browser caches this file, which actually contains a malicious ZIP archive.
The PowerShell script scans the local browser cache, extracts the hidden archive, and launches the malware from the local system without initiating any new web requests.
This method circumvents established security programmes that monitor network traffic or file downloads. The technique is being rapidly adopted by various threat actors, including ransomware gangs.
Action points
- It is critically important to never copy and paste text or commands provided by an external website into operating system dialogue boxes, terminal windows, or address bars.
- Organisationally, Endpoint Detection and Response (EDR) capabilities should be used that look for PowerShell scripts interacting with or manipulating browser cache files, or which execute in a hidden (headless) manner. These are clear indicators of this attack vector.
- Browsers and security software should restrict or audit the automatic execution of files retrieved from the browser cache by command-line utilities.
- Consider implementing’zero trust’ security policies that limit the execution of unrecognised executable files, even if they originate from what appears to be a local path, such as the extracted file from the cache.
Read more here.

