From thehackernews.com
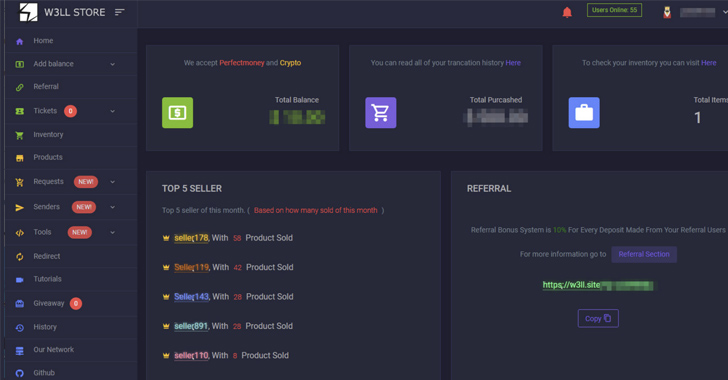
A previously undocumented “phishing empire” has been linked to cyber attacks aimed at compromising Microsoft 365 business email accounts over the past six years.
“The threat actor created a hidden underground market, named W3LL Store, that served a closed community of at least 500 threat actors who could purchase a custom phishing kit called W3LL Panel, designed to bypass MFA, as well as 16 other fully customized tools for business email compromise (BEC) attacks,” Group-IB said in a report shared with The Hacker News.
The phishing infrastructure is estimated to have targeted more than 56,000 corporate Microsoft 365 accounts and compromised at least 8,000 of them, primarily in the U.S., the U.K., Australia, Germany, Canada, France, the Netherlands, Switzerland, and Italy between October 2022 and July 2023, netting its operators $500,000 in illicit profits.
Some of the prominent sectors infiltrated using the phishing solution include manufacturing, IT, consulting, financial services, healthcare, and legal services. Group-IB said it identified close to 850 unique phishing websites attributed to the W3LL Panel during the same time period.