From thehackernews.com
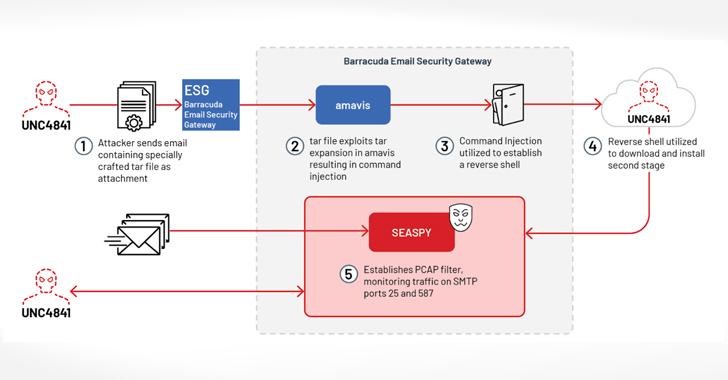
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Friday disclosed details of a “novel persistent backdoor” called SUBMARINE deployed by threat actors in connection with the hack on Barracuda Email Security Gateway (ESG) appliances.
“SUBMARINE comprises multiple artifacts — including a SQL trigger, shell scripts, and a loaded library for a Linux daemon — that together enable execution with root privileges, persistence, command and control, and cleanup,” the agency said.
The findings come from an analysis of malware samples obtained from an unnamed organization that had been compromised by threat actors exploiting a critical flaw in ESG devices, CVE-2023-2868 (CVSS score: 9.8), which allows for remote command injection.