From hackread.com
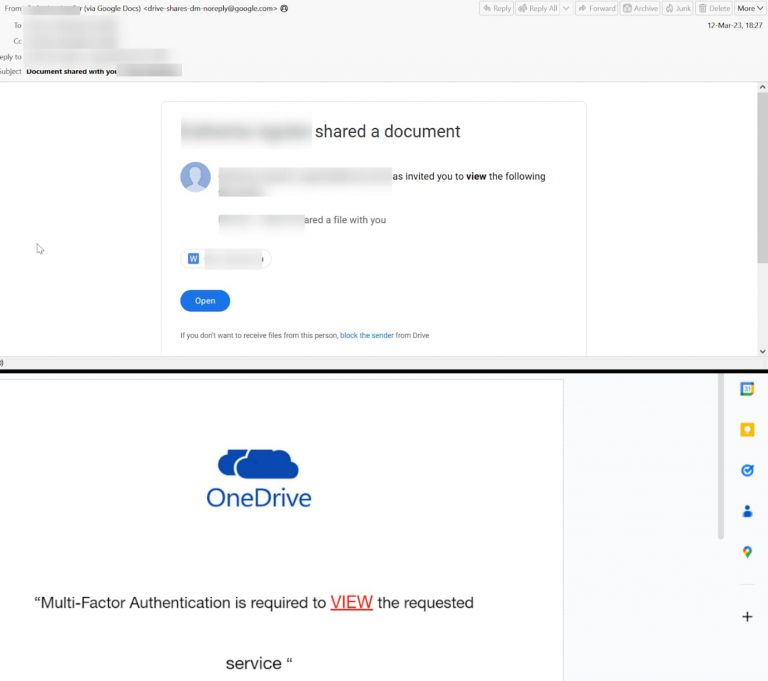
This attack starts with creating a Google document directly sent to the user via email from this spoofed NO-REPLY@GOOGLE.COM address.
Check Point researchers have discovered a new phishing scam campaign that distributes illegitimate URLs by exploiting Google Docs, with the aim of stealing the victim’s cryptocurrency credentials.
According to a research report authored by Jeremy Fuchs, a cybersecurity researcher, and analyst at Check Point Software, and shared with Hackread.com, Google Docs is the latest attack vector phishers are using to redirect users to credential harvesting sites.
Hackers Exploiting Google Docs Services to Distribute Malicious URLs
Check Point researchers observed that legit services of Google Docs are being exploited to send illegitimate messages or URLs, such as the email, pages, and comment features in Google Docs, which indicates the evolving nature of Business Email Compromise (BEC) campaigns.
Dubbing the campaign BEC 3.0, researchers wrote that using legit sites makes it easier for attackers to make their phishing attempts successful because it doesn’t raise any suspicion. In an attack analyzed by Check Point’s team, hackers sent links redirecting to bogus cryptocurrency sites.