From securityweek.com
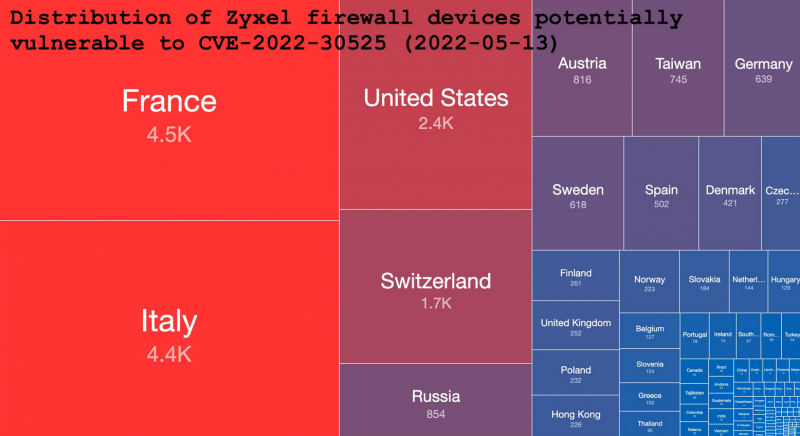
Exploitation attempts targeting a recently disclosed vulnerability affecting Zyxel firewalls started just one day after the flaw’s existence came to light.
Cybersecurity firm Rapid7 and Zyxel informed users on May 12 that Zyxel’s ATP, VPN and USG FLEX series business firewalls are affected by a critical vulnerability that can be exploited by a remote, unauthenticated attacker for arbitrary code execution as the “nobody” user.
The flaw, tracked as CVE-2022-30525, can be exploited through a device’s HTTP interface. Rapid7 has developed a Metasploit module and showed how an attacker could exploit the vulnerability to obtain a reverse shell.