From malware.news
You might want to read my prior articles on Android/BianLian first: unpacking, payload, fake server.
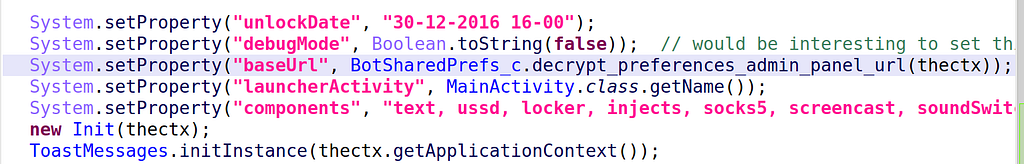
There was a remaining point which was bugging me: how does the Android/BianLian bot know where to contact the C&C?
Having worked on the samples for several days, I noticed they weren’t always heading to the same website: hxxp://rheacollier31532[.]website, hxxp://shanehook85484[.]website etc.
So, where do those names come from? Is this from a Domain Generation Algorithm (DGA)? or are they hidden in an asset?