From thehackernews.com
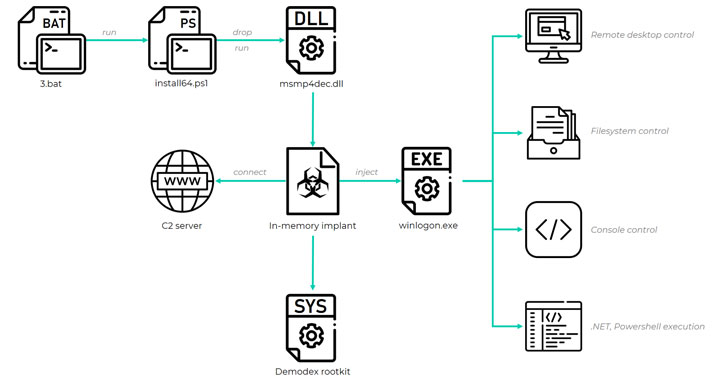
A formerly unknown Chinese-speaking threat actor has been linked to a long-standing evasive operation aimed at South East Asian targets as far back as July 2020 to deploy a kernel-mode rootkit on compromised Windows systems.
Attacks mounted by the hacking group, dubbed GhostEmperor by Kaspersky, are also said to have used a “sophisticated multi-stage malware framework” that allows for providing persistence and remote control over the targeted hosts.
The Russian cybersecurity firm called the rootkit Demodex, with infections reported across several high-profile entities in Malaysia, Thailand, Vietnam, and Indonesia, in addition to outliers located in Egypt, Ethiopia, and Afghanistan.